Recon-ng [Part One]
Recon-ng was built by Tim Tomes and is made with Python.
Open Terminal
Type the following in the terminal.
recon-ng

Main Screen

First Step
You should first start by typing the "help" command to see all the possible commands you can use.
help

List of commands

Show Modules
show modules
Application Programming Interface (API)
Recon-ng has an amazing feature that allows a hacker to extract recon information from known API's:
- Bing
- and others
To show what API keys that Recon-ng uses by typing the following:
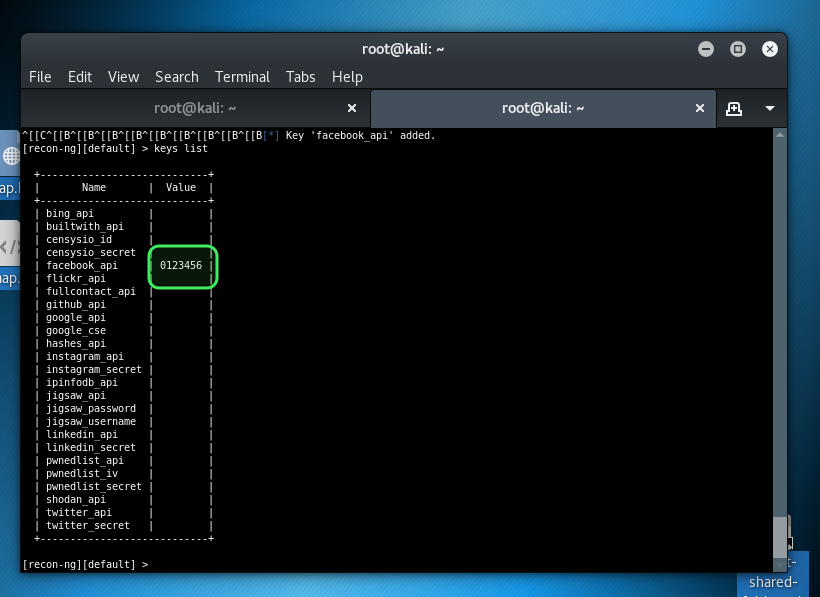
keys list


Add Keys
You obtain an API key from the site and add it to Recon-ng for use.
Example:
API key from Facebook and that key was "0123456"
keys add facebook_api 0123456

If you type "keys list" again you will see the key added to the list.
Using recon-ng
We are going to use one of recon-ng commands that don't require a api key.
Scanning for vulnerabilities
XSS (cross-site scripting) vulnerabilities
You will be typing in the following:
recon-ng > use recon/domains-vulnerabilities/xssposed
This will load the module into memory
Now type "show info"
show info
This command will show similar information that Metasploit shows.
Set Source
Type the following "set source" [using google.com as example]
set source
Now it's read to run
run
After the scan completes you will be given results and if nothing is showed up then it will appear as the following:
No vulnerabilities found.
